Example Descriptions
This page contains descriptions of real transaction payloads from past attacks, used as API test templates later in these docs, to illustrate how Redefine's Insights Engine can help detect and prevent malicious activities in web3 applications.
Transaction End-Point
| Example Name | Attack Description |
|---|---|
| OFAC Flag example | This example illustrates a hypothetical scenario where a user attempts to swap ETH for a token ("DreamCash") that is illiquid, highly concentrated, and owned by an address that is on the OFAC sanctions list. |
| Chads token example | This illustrates a prevalent DEX scam, showcasing how unsuspecting users are lured into swapping ETH for worthless tokens. |
| BadgerDAO example | On February 12, 2021, BadgerDAO fell victim to a sophisticated cyber attack. An intruder gained access to the organization's Cloudflare account, uploading malicious code. This code deceitfully prompted users to authorize the attacker's wallet, leading to a staggering theft of $120 million. |
| AZUKI scam example | In a deceptive NFT scam, a fraudster used Twitter to advertise a fake NFT minting event. Unwitting participants, believing they were minting Azuki NFTs, signed transactions that inadvertently sent ETH to the scammer's wallet, resulting in a substantial loss of funds. |
Message End-Point
| Example Name | Attack Description |
|---|---|
| NFT listing on Opensea example | Exploiting a scheduled update in Opensea contracts, the scammer orchestrated a phishing attack. By mimicking Opensea's official email, the attacker misled users into unwittingly listing their NFTs for free, subsequently acquiring them at no cost and absconding with assets worth $1.7 million. |
| CowSwap swap example | In this attack, the attacker changed the receiver address of the swap funds to an unwanted recipient. |
How to Test Examples?
Discover how the DeFirewall API evaluates real-world attack scenarios by using our pre-constructed templates. Access these examples through the 'EXAMPLES' drop-down in the API Reference. Select an example to initiate a test, and observe the API's capability in identifying and flagging diverse security risks.
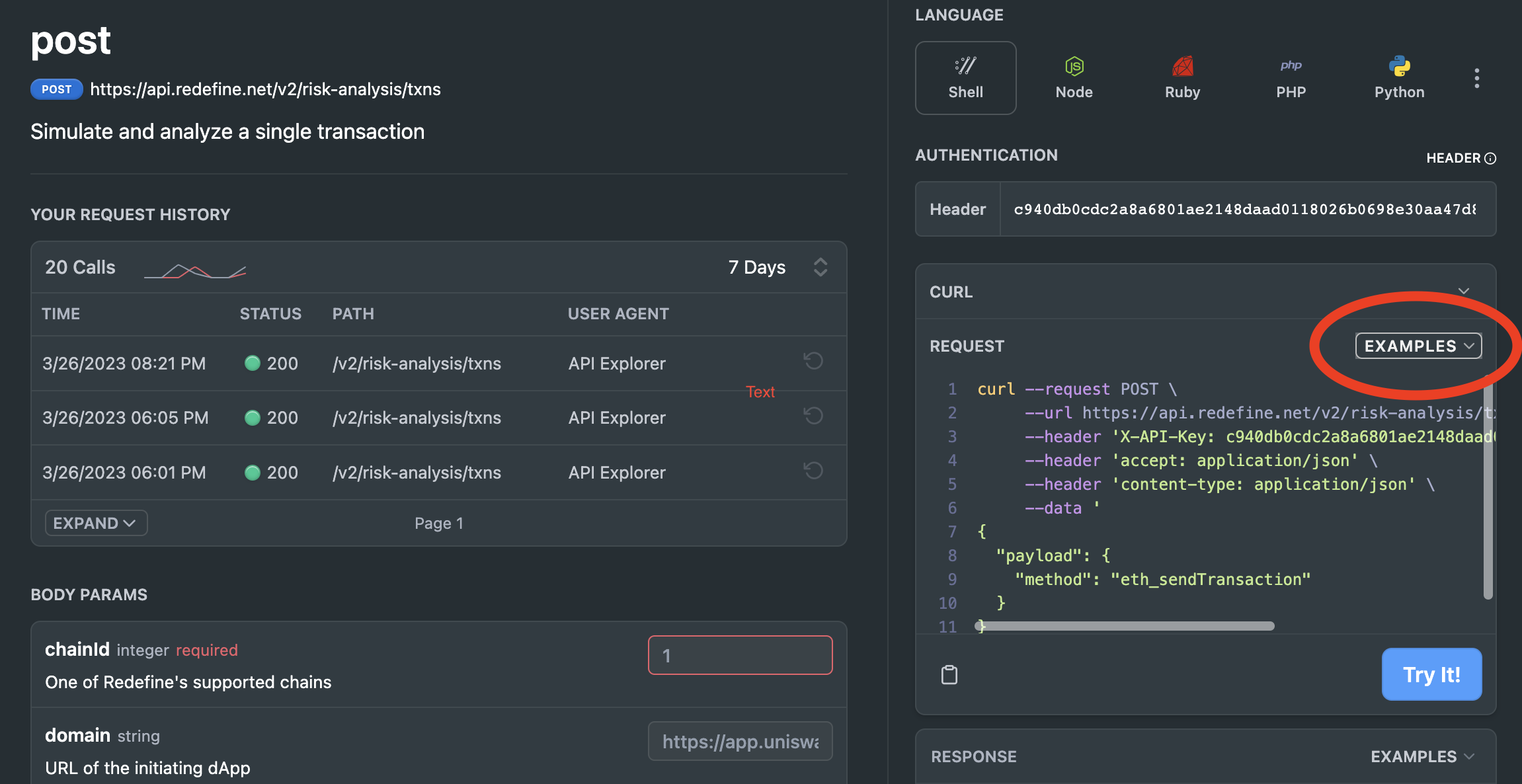
Press one of the examples for it to prepare the API call.
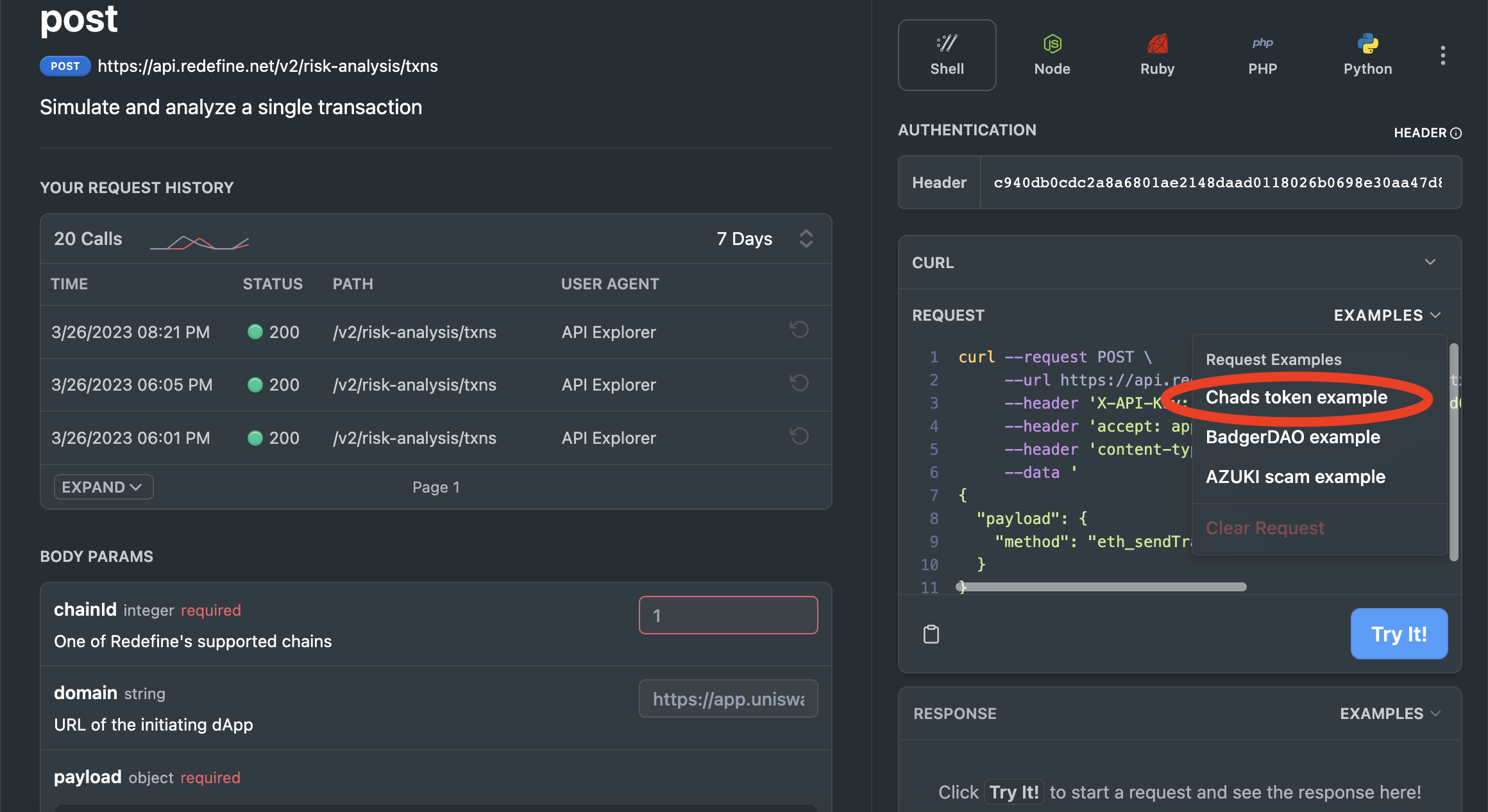
Lastly, press "Try It!"